-
On this page
The Office of the Australian Information Commissioner (OAIC) has prepared this guide to assist Australian Government agencies and private sector organisations (entities) prepare for and respond to data breaches in line with their obligations under the Privacy Act 1988 (Cth) (Privacy Act).
The guide is in five parts.
Part 1: Data breaches and the Australian Privacy Act
This section outlines the requirements of the Privacy Act that relate to personal information security and data breach response strategy. The principles contained within the Privacy Act for the handling of personal information may be adopted by any entity to lower the risk of a data breach occurring and to effectively reduce the impact of a data breach.
Part 2: Preparing a data breach response plan
The faster an entity responds to a data breach, the more likely it is to effectively limit any negative consequences. A data breach response plan is essential to facilitate a swift response and ensure that any legal obligations are met following a data breach.
Part 3: Responding to data breaches — four key steps
An effective data breach response generally follows a four-step process — contain, assess, notify, and review. This section outlines key considerations for each of these steps to assist entities in preparing an effective data breach response.
Part 4: Notifiable Data Breaches
This section outlines the requirements of the NDB scheme under the Privacy Act. The NDB scheme contains mandatory data breach reporting obligations in relation to certain data breaches, and requirements to assess suspected data breaches.
Part 5: Other sources of information
The obligations of the Privacy Act in relation to data breaches co-exist with other reporting obligations. This section assists entities in identifying where they can find information about other data breach reporting requirements.
Who should use this guide?
Any entity that handles personal information can use this guide to inform their preparation and response strategy for a data breach.
However, this guide is primarily targeted at entities that have obligations under the Privacy Act to protect personal information. These entities are required to take reasonable steps to protect the personal information that they hold, and may be required to notify affected individuals and the Australian Information Commissioner (Commissioner) of a data breach under the NDB scheme.
How to use this guide
Different parts of this guide will be of greater or lesser relevance to different entities depending on their goals.
Entities seeking a greater understanding of the Privacy Act, specifically in how the Privacy Act’s requirements relate to personal information security and data breach management responsibilities, should refer primarily to Part 1 and Part 4.
Entities that want to prepare a data breach response strategy, or review the effectiveness of their current response plan, should refer primarily to Part 2 and Part 3.
Entities that have experienced a data breach can refer to Part 3 to understand the main components of an effective data breach response. They should also refer to Part 4, as it provides guidance on the mandatory data breach reporting and assessment requirements of the NDB scheme.
A cautionary note
There is no ‘one size fits all’ solution to preparing for and responding to data breaches. This guide does not provide detailed information about the systems or processes an entity may put in place to manage data breaches.
Further, this guide does not provide detailed information about other obligations that may apply to entities in addition to the Privacy Act. Entities should consider their privacy obligations alongside other relevant legal requirements and standards.
The guide does not constitute or replace legal advice on obligations under the Privacy Act. It is published by the Commissioner to provide general information to help entities meet the requirements of the Privacy Act. Entities are encouraged to seek professional advice tailored to their own circumstances where required.
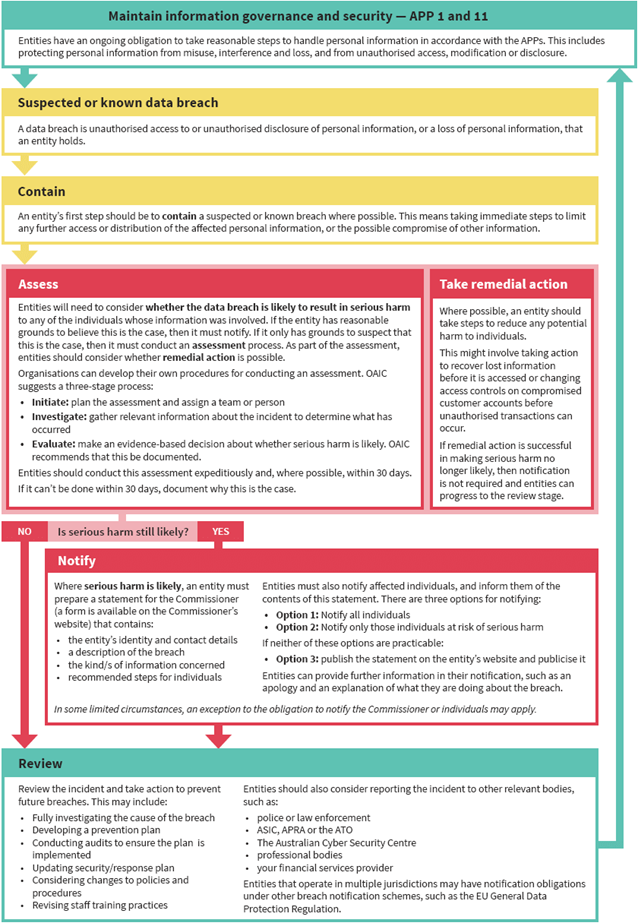
The data breach response flowchart
The following flowchart summarises the general steps that entities may need to take in a data breach response process.
As each data breach is a unique event that involves different root causes, types of personal information, and risks of harm, the steps and actions required of entities are likely to differ for each incident.
Every data breach needs to be dealt with on a case-by-case basis, with an understanding of:
- the risks posed to affected individuals by that breach and;
- the actions that would be most effective in reducing or removing those risks.
Generally, the actions taken following a data breach should follow four key steps:
Step 1: Contain the data breach to prevent any further compromise of personal information.
Step 2: Assess the data breach by gathering the facts and evaluating the risks, including potential harm to affected individuals and, where possible, taking action to remediate any risk of harm.
Step 3: Notify individuals and the Commissioner if required. If the breach is an ‘eligible data breach’ under the NDB scheme, it may be mandatory for the entity to notify.
Step 4: Review the incident and consider what actions can be taken to prevent future breaches.
These steps are explained in further detail in Part 3 of this guide, and the steps that are required by the NDB scheme (coloured red) are explained in Part 4.