-
On this page
Assessment undertaken: June 2017
Draft report issued: October 2017
Final report issued: March 2018
Part 1: Executive summary
1.1 This report outlines the findings of the Office of the Australian Information Commissioner’s (OAIC) privacy assessment of Trulioo’s handling of personal information as a gateway service provider (GSP) of the Document Verification Service (DVS).
1.2 The purpose of this assessment was to establish whether Trulioo is:
- collecting personal information in accordance with Australian Privacy Principle (APP) 3
- notifying individuals of the collection of personal information in accordance with APP 5
- taking reasonable steps to secure the personal information collected and held in its systems and databases in accordance with APP 11.
1.3 This assessment finds that:
- the Trulioo staff that the OAIC interviewed demonstrated a strong understanding of their privacy and confidentiality responsibilities, and their information security obligations
- Trulioo has a number of documented policies and procedures, and some of these documents can be improved
- Trulioo may wish to consider whether and how individuals can be more clearly notified of Trulioo’s role and involvement in the DVS.
1.4 The OAIC has made one recommendation in this assessment to address a medium level privacy risk. The recommendation relates to improving Trulioo’s information security documentation.
Part 2: Introduction
Background
2.1 The DVS is a national online system that allows agencies or organisations to collect personal information from an identity document presented by an individual, with their consent, and compare it against the original record of the document held by the Government agency that issued the document (issuing agency). Identity documents that can be verified by the DVS include, but are not limited to, passports and visas, birth certificates, driver licences, and Medicare cards. These verifications are conducted in real time to inform decisions that rely upon the confirmation of a person’s identity.
2.2 The Attorney-General’s Department (AGD) is responsible for the development and operation of the core technical components of the DVS.
2.3 The DVS has been available to government agencies since 2009. Since that time, additional access arrangements have allowed limited commercial access for businesses operating under legislated client identification requirements. In this assessment, the term ‘business user’ refers only to these commercial users of the DVS, as Trulioo does not at this time provide a gateway service to government agencies.
2.4 All business users of the DVS must meet the eligibility criteria contained in the DVS Access Policy and Guidelines,[1] and abide by the DVS Terms and Conditions of Use.[2] Business users must access the DVS through an approved GSP, or successfully apply to the AGD to become a GSP in their own right.
2.5 Trulioo is an approved GSP. As such, its responsibilities include:
- establishing a functional connection to the DVS which can be used by business users to match identity information
- assessing the eligibility of business users to use the DVS, and advising the AGD
- ensuring that business users meet the consent requirements for accessing the DVS
- attaching the DVS Terms and Conditions of Use to contracts with its business users.
Overview of the document verification process
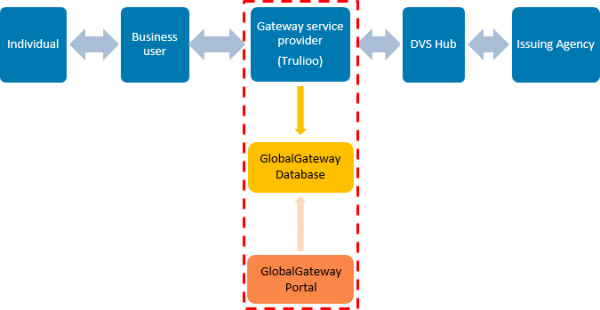
2.6 The primary components of the document verification process include an individual, a business user, a GSP, the DVS ‘Hub’, and an issuing agency.
2.7 An individual presents personal information to a business user as evidence of their identity. This is usually done as part of an application for goods or a service, such as applying for a bank loan or enrolling into an educational institution. This personal information includes the individual’s full name, date of birth, and a government related identifier.[3] The government related identifier varies depending on the issuing agency relied on. For example, it may be a driver’s licence, passport, or Medicare number.
2.8 The business user enters the individual’s personal information into one of their computers. A GSP connects the business user to the DVS Hub, and directs the personal information to that Hub.
2.9 The DVS Hub securely directs that personal information to the issuing agency.
2.10 The issuing agency performs an automated check of its data to confirm whether the information provided to the business user matches the information it holds.
2.11 The issuing agency sends an automated response back to the DVS Hub, indicating that the information provided was matched, not matched, invalid, or that there was a system error of some kind.
2.12 The GSP transmits that response from the DVS Hub back to the business user. Figure 1 (below) sets out this document verification process.
Trulioo
2.13 Trulioo is a global identification verification company ‘providing advanced analytics’ based on ‘information such as public records, credit files, and government data’.[4]
2.14 In connecting its business users to the DVS Hub, Trulioo allows them to choose which issuing agencies they want to rely on, based on their business needs and the purposes for which the verification is being made. For example, one business user may choose to verify an individual’s passport, birth certificate, and Medicare card. Another business user may only require the verification of a driver’s licence.
GlobalGateway
2.15 GlobalGateway is Trulioo’s instant electronic identity verification service that performs Trulioo’s role in the document verification process. Once Trulioo has approved a business user, the business user can collect the relevant personal information from individuals. GlobalGateway then matches the personal information provided against the information held by the business user’s chosen issuing agencies.
2.16 There are two ways in which a business user can integrate and use the GlobalGateway product: Normalized API and XML Direct. The OAIC understands that the vast majority of Trulioo’s business users opt to integrate GlobalGateway through Normalized API,[5] and so has focussed on Normalized API in this report.
2.17 The Normalized API integration method allows business users to customise and embed GlobalGateway into their website. Business users notify individuals that their personal information is being collected, and the individual must provide consent before they are able to proceed with the identity verification transaction. Business users can choose the wording to notify the individual of the collection and use of their personal information.
Back end systems
GlobalGateway database
2.18 Trulioo’s GlobalGateway processes personal information relating to the individuals being verified, such as their name, date of birth, address, and government related identifier. It responds with an identity verification result, such as that their identity was matched or not matched by the issuing agency. The GlobalGateway database stores this information where required by legislation or business user specifications.
2.19 The physical components of the GlobalGateway database are held in data centres in Australia, and hosted by Trulioo’s third party providers.
GlobalGateway Portal
2.20 The GlobalGateway Portal is an interface that connects to the GlobalGateway database. The GlobalGateway Portal provides a way for GlobalGateway business users with certain system privileges to securely access records of their own identity verification activities. These records include logs of completed GlobalGateway identity verification transactions with that business user. The details listed include the unique ID relating to that transaction, the individual’s identity verification result, and if directed by the business user, personal information such as their name, date of birth, address, and government related identifier. GlobalGateway business users can search their records based on the transaction ID, or can export general records for reporting, auditing, or other purposes.
2.21 Trulioo staff with certain privileged rights can also access data stored in the GlobalGateway database through their version of the GlobalGateway Portal. They are able to access and run queries on these transaction records for reporting or auditing purposes, or by request from business users. Figure 1 (below) sets out this GlobalGateway Portal access to the Global Gateway database.
Figure 1 — The document verification process
Part 3: Findings
Collection of personal information
3.1 Under APP 3, an APP entity may only collect solicited personal information where it is reasonably necessary for, or directly related to, the entity’s functions or activities. APP 3.6(b) states that an APP entity must collect personal information about an individual only from that individual, unless it is unreasonable or impracticable for the entity to do so.
Observations
3.2 Trulioo’s GlobalGateway product supports ‘a diverse range of international electronic identity verification requirements’, and its business users use it for their ‘compliance, risk mitigation and age verification needs’.[6]
3.3 Trulioo’s business users require an individual to provide their personal information, which Trulioo collects through GlobalGateway. For example, if an individual provides an Australian passport, the personal information that will be collected includes their name, date of birth, and passport number. The business users then input the individual’s personal information into the GlobalGateway product via their chosen integration method, which is most commonly the Normalized API.
3.4 Trulioo has due diligence procedures in place to consider whether the collection of solicited personal information is also reasonably necessary for, or directly related to, any business user’s functions or activities, prior to approving a new Trulioo business user.
Analysis
3.5 The OAIC considers that Trulioo’s collection of personal information is directly related to and consistent with its purposes and functions as a GSP. In addition, Trulioo has processes in place to ensure that the collection of personal information by any of their new business users will be reasonably necessary for, or directly related to, that business user’s functions or activities. Trulioo also ensures that their business users meet the access criteria for the DVS.
3.6 Personal information passes from the individual through to Trulioo’s systems indirectly, via the business user’s chosen GlobalGateway integration method on their website. However, the personal information is solicited by the business user, as part of their document verification requirements.
3.7 Due to the nature of the DVS, GSPs are not in direct contact with an individual. The OAIC considers that it would be unreasonable or impracticable for Trulioo to collect personal information only and directly from the individual, without the involvement of the business user in the collection process.
Notification of the collection of personal information
3.8 Under APP 5, an APP entity that collects personal information about an individual must take such steps (if any) as are reasonable in the circumstances either to notify the individual of the matters under APP 5.2 or to ensure the individual is aware of those matters. These matters include:
- the APP entity’s identity and contact details
- the fact and circumstances of collection
- whether the collection is required or authorised by law
- the purposes of collection
- the entity’s usual disclosures of personal information of the kind collected by the entity
- information about the entity’s APP Privacy Policy.
3.9 The APP entity must take reasonable steps at or before the time of collection, or, if that is not practicable, as soon as practicable after the collection. This applies to all personal information collected about an individual, either directly from the individual or from a third party.
3.10 The APP 5 requirement to notify individuals about the collection of their personal information is supported by the DVS Terms and Conditions of Use. Under these terms and conditions, GSPs and business users must be subject to the Privacy Act. Business users must also ensure that individuals are informed of the purpose for which their personal information is sought, and that the process of identity verification may involve the use of third party systems and services. Individuals must also provide their express consent for the use of their personal information for that purpose. GSPs are required to ensure that business users are following these consent requirements under the DVS Terms and Conditions of Use that apply to GSPs.[7]
Observations
3.11 Personal information is first collected through a business user, as part of that business user’s requirements, before being collected by Trulioo, as a GSP. The business user, as the front line of the interaction with the individual, provides the notification of the collection of personal information. They generally do this through a notification statement on their website. In addition, the individual must provide consent, generally through ticking a consent box, before the identity verification transaction can proceed.
3.12 The OAIC understands that Trulioo requires business users to notify individuals that their personal information will be collected and processed by a third party, without naming Trulioo specifically. Trulioo advised the OAIC that, if an individual enquires with a business user about the identity verification process, the business user would refer the individual to Trulioo where appropriate.
Analysis
3.13 APP Entities must take reasonable steps to notify individuals of the matters under APP 5.2. What is reasonable in Trulioo’s circumstances involves a consideration of its purposes as a GSP, and the practicalities of notifying an individual through a business user’s platform.
3.14 Trulioo must take such steps (if any) as are reasonable in the circumstances to notify the individual that it has collected their personal information.[8] Trulioo collects this information from business users, rather than from the individuals directly.
3.15 With the Normalized API, Trulioo’s business users can choose the wording to notify an individual at the point of collection of personal information. The business users may refer to Trulioo or the GlobalGateway product by name. However, this is not obligatory. In the circumstances where the business users choose not to specifically name Trulioo, we consider there is a limited chance that an individual will be alerted to Trulioo’s role in the collection process, or the fact that it holds their personal information.
3.16 An example of a privacy protective measure that Trulioo could take so that business users notify the individual of the relevant APP 5 matters on its behalf would be forming enforceable contractual arrangements. Onboarding a new business user could be contingent on them disclosing Trulioo’s role at some point in the identity verification process, for instance, in the business user’s privacy policy. This would assist individuals to understand how Trulioo will handle their personal information, as collected by the business user.
3.17 The OAIC also notes that, under APP 5.1, it may be reasonable in some circumstances for an APP entity like Trulioo to not take any steps to provide notification of all or some of the APP 5 matters.
3.18 The OAIC’s APP Guidelines note that one circumstance where taking no steps may be reasonable is where the individual is aware that personal information is being collected, the purpose of collection and other APP 5 matters relating to the collection. Individuals who provide their personal information to a Trulioo business user for the purposes of verifying their identity would generally be aware that the information is being collected and used for that purpose.
3.19 The OAIC also notes that the DVS Terms and Conditions of Use specify that consent must be obtained from the individual before their personal information can be collected and used in an identity verification transaction.
3.20 During this assessment the OAIC also considered that Trulioo, as a GSP, could be characterised as an intermediary in the overall identity verification process that involves the DVS. The OAIC recognises that, in general, there are limitations in notifying individuals of every intermediary through which their personal information passes in an interconnected network that supports a particular transaction.
3.21 Ultimately, however, the OAIC took the view that Trulioo’s role as a GSP is more than an intermediary through which personal information passes because Trulioo retains personal information in the GlobalGateway database. Trulioo is retaining this personal information for legitimate business purposes.
3.22 The fact that Trulioo retains some personal information about individuals from an identity verification transaction activates other obligations under the APPs, such as the obligation to provide an individual with access to personal information that Trulioo holds about them under APP 12. While APP 12 was not directly within the scope of this assessment, an individual would not be aware of the rights available to them, such as the right to request access from Trulioo under APP 12, unless they are proactively notified of Trulioo’s role in the identity verification transaction under APP 5.
3.23 As a result, the OAIC considers that Trulioo is technically under an obligation to notify individuals that they are collecting their personal information under APP 5. It follows that there is some risk that Trulioo’s current notification practices may breach APP 5.
3.24 The OAIC considers that the level of risk relating to Trulioo’s notification practices is low at the present time. While there is scope to enhance practices, the OAIC notes that, although Trulioo may not be named in all instances where personal information is collected, the requirements of the DVS Terms and Conditions of Use ensure that individuals are aware of the purpose for which their personal information is being collected, and that consents is provided.
3.25 To improve its privacy practices in this area, the OAIC suggests that Trulioo consider whether individuals can be more clearly notified of Trulioo’s collection and retention of personal information, such as by taking the measures described at 3.16.
3.26 Finally, the Privacy Amendment (Notifiable Data Breaches) Act 2017 established a Notifiable Data Breaches (NDB) Scheme in Australia. The NDB Scheme commenced on 22 February 2018. Under the NDB Scheme, organisations covered by the Privacy Act are required to notify any individuals likely to be at risk of serious harm by a data breach, as well as the OAIC. The NDB Scheme may be another factor for Trulioo to take into consideration in updating or improving its notification practices and documentation in this area, particularly with regard to establishing clear lines of communication and responsibility with its business users in the event that one or more links in the DVS information flow are subject to a data breach in the future.
Security of personal information
Our approach
3.27 The OAIC’s Guide to Securing Personal Information provides guidance on the steps and strategies entities may take to protect personal information in accordance with APP 11. The privacy analysis in this section of the report considers the way in which Trulioo implements these steps and strategies when handling personal information collected for DVS purposes.
Governance, culture and training
Observations
3.28 The responsibility for the operation, maintenance, and marketing of GlobalGateway is allocated to a number of teams within Trulioo, which consists of approximately 40 employees. Trulioo’s management team includes the Chief Executive Officer, the General Manager, and the Vice President of Technology. Other staff include the Manager of Information Assurance and Compliance, GlobalGateway system administrators, system engineers, and marketing, sales, and business user service teams.
3.29 Trulioo has a documented governance structure relating to its Information Security Management System (ISMS).[9] Within that governance structure, the most senior level of management is responsible for:
- the strategic direction of information security
- approving risk treatment plans of business security risks
- supporting the implementation and sustainability of the ISMS
- ensuring compliance with legislation and contracts.
3.30 The General Manager and Vice President of Technology are responsible for reviewing and approving business and administrative policies and controls, and supporting the implementation and sustainability of the ISMS.
3.31 The Manager of Information Assurance and Compliance is responsible for developing and maintaining standards, guidelines, and procedures to support the ISMS, and for managing and monitoring information security and compliance. Lower management is responsible for ensuring that their staff adhere to the ISMS.
3.32 Staff training includes mandatory induction training on compliance, handling personal information, and accessing and managing information and information technology resources. This includes training on the APPs. There are also annual refresher courses which all staff must complete, and staff are sent monthly newsletters and reminders relating to privacy and security issues.
Analysis
3.33 The OAIC considers that there are clearly defined teams within Trulioo that are responsible for the development, operation, maintenance, and support of the GlobalGateway product.
3.34 The Trulioo staff that the OAIC interviewed demonstrated a strong understanding of the GlobalGateway product, their privacy and confidentiality responsibilities, and their information security obligations.
Internal practices, procedures and systems
Observations
3.35 Trulioo provided the OAIC with high-level, company-wide documentation, such as the ISMS, Information Security Policy (ISP), and Privacy Policy.
3.36 The purpose of the ISP, which was created as part of the ISMS, is to ‘maintain the confidentiality, integrity, and availability’ of Trulioo’s ‘information assets, information systems, and services’, through:
- management and business processes that include and enable security processes
- ongoing personnel awareness of security issues
- physical security requirements for information systems
- governance processes for information technology
- reporting information security events and weaknesses
- creating and maintaining business continuity plans
- monitoring for compliance.
3.37 The ISP outlines operational policies, standards, guidelines, and procedures, and, at times, refers to separate, secondary documentation for further guidance. For example, according to the ISP, password management systems must be interactive and ensure quality passwords, and the allocation of passwords must be controlled through a formal management process.
3.38 The ISP then refers staff to the separate Password Guidelines document. The Password Guidelines detail the program that staff are to use to generate and manage their passwords, and provides further guidance on choosing a strong password to meet Trulioo’s minimum password requirements.
3.39 Trulioo also provided the OAIC with GlobalGateway-specific documentation, such as the Secure System Engineering Principles, Incident Management Procedure, Business User Registration Process, Troubleshooting Procedures, and Due Diligence Checklist.
3.40 The OAIC considered an Audit Report relating to an ISO 27001:2013 certification process,[10] and Trulioo’s corresponding RACI chart.[11] The OAIC also viewed a recent Audit Report relating to a vulnerability assessment and penetration test of the GlobalGateway system. [redacted].
3.41 According to the ISMS, Trulioo must conduct annual reviews and updates of the ISMS and its supporting documentation (including policies, standards, guidelines, and procedures). These revisions must be approved by the Vice President of Technology and the General Manager. The OAIC understands that in practice some policies are updated on a quarterly basis.
3.42 However, the OAIC observed that, while some documents have been regularly reviewed, this is not done consistently across all documentation. For example, the ISP was created in May 2015, and was not reviewed and updated until June 2017. The ISMS was created in April 2015, and had not been reviewed since October 2015. The Incident Management Procedure was created in December 2014, and updated in 2015 and 2017, but not 2016.
Analysis
3.43 Trulioo’s documentation of the roles and responsibilities for implementing the ISO controls 27001:2013 controls, in its RACI chart, is good practice. In addition, Trulioo has promptly mitigated or removed the risks identified by audit reports, which is a good strategy to ensure the maintenance or improvement of the security of GlobalGateway.
3.44 Trulioo’s ISMS is a clear, overarching policy document. The ISP, which is part of the broader ISMS, details Trulioo’s policies relating to information security. The ISP then refers to secondary documentation, such as the Password or Acceptable Use Policy, which further details these general policies or procedures.
3.45 While this multi-layered approach to documentation is good information security practice, there were instances where the documentation was not reviewed for more than one year. The OAIC considers that there is a risk that the information security documentation may not continue to reflect Trulioo’s current security practices if the documentation is not reviewed and updated according to the regular intervals Trulioo has nominated. The OAIC recommends that Trulioo put additional processes in place to ensure the timely review and update of all policy documentation.
The OAIC also considered that there 3.46 were some content gaps in the documentation of Trulioo’s practices, such as the documentation relating to Trulioo’s cryptographic practices. [redacted].
3.47 This general approach to cryptography aligns with good information security practices. However, the ISP does not refer to any secondary documentation. [redacted].
3.48 [redacted].
3.49 The potential risks of a suite of information security documents that are not linked together includes new or less experienced staff being unaware of the full extent of Trulioo’s processes and procedures. If the Trulioo staff that operate on a daily basis within these processes and procedures, such as those relating to cryptography, were to leave unexpectedly, there is a risk that less experienced staff may not have appropriately detailed documentation to refer to.
3.50 Having a comprehensive and easy to follow suite of information security documents will become increasingly important as Trulioo’s operations expand. The OAIC considers that there is a medium risk of breaching APP 11 if some content gaps in supporting documentation are left unchecked. The OAIC recommends that Trulioo reviews its information security documentation, and where necessary creates and implements detailed written policies that further support the broader ISMS and ISP.
Recommendation 1
Trulioo:
- ensures the consistent and timely review of its information security documentation
- creates and implements detailed policies, as needed, to further support its high-level documentation, and disseminates these policies to staff.
Third party providers
Observations
3.51 Trulioo relies on a number of third party providers to assist in physical and virtual hosting of the GlobalGateway product.
3.52 The physical servers of the GlobalGateway product are hosted in multiple data centres, across different locations. Trulioo has two primary third party providers that manage different aspects of the servers, as well as hosting the GlobalGateway virtual environment.
3.53 The OAIC has viewed portions of the formal service level agreements (SLAs) that Trulioo maintains with these third party providers. These SLAs and the Incident Management and Troubleshooting Procedures detail the procedures for responding to system incidents of varying severity. Trulioo’s third party providers would be responsible for monitoring, alerting, and responding to a physical failure of one of the datacentres.
3.54 Trulioo’s Incident Response Team would be ultimately responsible for managing the incident and maintaining information security, and Trulioo’s Executive-level management would be responsible for providing the final GlobalGateway failover order. This means that, even if an entire data centre location was to fail, the GlobalGateway system could be switched to the standby disaster recovery system, located in another data centre.
3.55 Trulioo also contracts other third party providers, such as for services relating to cloud computing and data security. These are discussed further in the ‘ICT Security’ section of this report.
Analysis
3.56 The OAIC did not identify any issues in relation to Trulioo’s use of third party providers in this assessment, and notes that the use of formal documentation, which outlines each party’s obligations is good practice.
ICT security
Observations
3.57 As noted at 3.29 and 3.35-3.36, Trulioo provided the OAIC with a broad range of documentation, much of which relates to its ICT security infrastructure.
3.58 Briefly, the mechanisms that are used to secure the GlobalGateway product and the personal information that it handles include network and software security controls, anti-virus and malware protections, patching, encryption, backing up, and testing.
3.59 The ISP notes that the servers that host Trulioo’s ICT systems are protected by a range of security controls, such as:
- [redacted]
- [redacted]
- [redacted]
- [redacted]
- [redacted]
- [redacted].
3.60 [redacted].
3.61 [redacted].
3.62 The ISP states that anti-virus or anti-spyware software ‘must be installed, regularly updated and consistently used’. The OAIC understands that Trulioo and its third party providers implement anti-virus and malware protections, both on the networks and on devices, and that these are updated regularly.
3.63 Trulioo performs patching, which is a security mechanism to address vulnerabilities in software applications as they arise. [redacted].
3.64 Cryptography helps to protect stored data or data in transit from unauthorised disclosure or use. The aspects of Trulioo’s ICT systems or networks that are protected by cryptography include:
- [redacted]
- [redacted]
- [redacted].
3.65 As noted at 2.19, GlobalGateway data is held in data centres that are hosted by third party providers. There are a number of failover processes in place to ensure that there is no significant data loss, should there be a GlobalGateway system failure.
3.66 The ISP states that backup and recovery processes must be tested regularly, and access to backup data is restricted to authorised users in compliance with access control requirements.
3.67 The ISP states that the principle of least privilege should be applied to the installation of new software. The OAIC understands that, in practice, only administrative accounts are authorised to install new software. [redacted].
3.68 GlobalGateway has separate development, testing, and operational environments. In accordance with the ISP, all changes to the GlobalGateway system are first developed and tested, before being implemented into the production environment.
3.69 In addition to separating its test and production environments, Trulioo performs testing of its overall systems. [redacted]. The OAIC has viewed examples of penetration and vulnerability testing.
Analysis
3.70 Generally, Trulioo’s use of a number of security mechanisms, such as anti-virus, patching, cryptography, and testing, represent good ICT security practice. [redacted].
3.71 There are some content gaps in Trulioo’s documentation, which details these practices. For example, the ISP and an SLA with a third party provider both refer to the need to implement anti-virus and malware protections. While interviews with Trulioo staff explored the specific software and systems that Trulioo uses, the OAIC has not reviewed any documentation which records this, or the schedule for updating it. Recommendation 1 addresses this issue.
3.72 [redacted]. The OAIC notes that Trulioo’s policies and procedures on patching are not documented in the ISP. Trulioo’s use of cryptography is another ICT security control that would benefit from specific, supporting documentation. The OAIC also notes that Trulioo’s practice for controlling the installation of new software is not itemised in the ISP. Recommendation 1 also addresses this issue.
Access security
Observations
3.73 According to the ISP, access to the GlobalGateway system and its data for Trulioo staff is determined by role. This means that staff must only be provided with access to the network and network services that they have been specifically authorised to use.
3.74 All staff are assigned user identifiers as per a formal user registration and de-registration process. Network access to Trulioo systems is revoked if the individual no longer requires that access.
3.75 [redacted]. Multi-factor authentication[12] is used for all privileged and administrative access.
3.76 [redacted].
3.77 The ISP outlines Trulioo’s general policy that passwords must be used and the allocation of passwords must be controlled through a formal management process. The separate Password Guidelines document further details Trulioo’s password policy. For example, all Trulioo staff are required to use a password management program, which ensures that system and website passwords meet complexity and length requirements [redacted].
3.78 [redacted].
3.79 All new Trulioo staff are subject to screening and background security checks.
3.80 According to the ISP, Trulioo performs system logging and monitoring for all ICT systems and resources that support GlobalGateway. [redacted].
3.81 Trulioo uses a monitoring program to filter and analyse logs. The program records activity by all users, and performs investigative and diagnostic processes to identify potential security incidents and review system access controls.
Analysis
3.82 Trulioo’s access controls, such as role-based access, multi-factor authentication, background security checks, and activity logging, are good security practices.
3.83 The ISP outlines many of these access controls. The OAIC identified some gaps in the documentation of these policies. For example, the ISP states that ‘additional security measures and controls must be applied to mobile devices’. While the OAIC understands from interviews with Trulioo staff that these measures and controls (such as those discussed at 3.78) are done in practice, the OAIC again refers to Recommendation 1 to ensure that Trulioo’s security practices are supported by policy documents.
Data breaches
Observations
3.84 The ISP outlines Trulioo’s policies on information security incident management. For example:
- all personnel must receive training related to incident management
- responsibilities and escalation processes must be clearly defined and documented
- information security events must be reported through appropriate management channels as quickly as possible
- personnel using information systems must note and report any observed or suspected information security weaknesses in those systems
- information security incidents must be responded to in accordance with the documented procedures
- the information gained from evaluation of information security incidents must be used to improve applicable information systems, policies, and procedures.
3.85 The Incident Management Procedure is a supporting document which supports the higher-level ISP. It details the processes and provides examples for carrying out the above policies in practice, such as incident reporting, severity determination, responding to an incident, recovery, and the post-incident phase, which looks to the lessons learned.
Analysis
3.86 The OAIC did not identify any issues in relation to Trulioo’s data breach or incident response plans in this assessment. The OAIC notes that the use of high-level policy documentation with detailed supporting procedures is good practice.
Physical security
Observations
3.87 The OAIC conducted the fieldwork component of this assessment via videoconference, and did not conduct physical inspections of Trulioo’s Vancouver office or the data centres, which host the GlobalGateway ICT environment. The OAIC understands that the physical security of Trulioo’s premises are audited annually by an external party.
3.88 The ISP outlines Trulioo’s policies for the security of its areas and equipment. For example:
- security perimeters must be defined
- secure areas must be protected by appropriate entry controls to ensure that only authorised personnel are allowed access
- access points must be controlled
- equipment must be sited and protected to reduce the risks from environmental threats, power failures, and unauthorised access.
3.89 Trulioo’s third party providers that host the physical components of the GlobalGateway system also manage the data centre’s physical security controls. [redacted].
3.90 Apart from in the ISP, the OAIC understands that these physical security controls are detailed in the relevant SLAs between Trulioo and their third party providers.
3.91 The OAIC understands that the physical security controls at Trulioo’s Vancouver office include [redacted].
Analysis
3.92 The OAIC did not identify any issues relating to the physical security surrounding either the datacentres or the Trulioo office in this assessment.
Destruction and de-identification
3.93 An APP entity must take reasonable steps to destroy or de-identify personal information if it no longer needs the information for any purpose for which it may be used or disclosed.
3.94 The reasonable steps that an organisation should take to destroy or de-identify personal information depends on a number of circumstances, including the amount and sensitivity of the personal information, the nature of the organisation, the organisation’s information handling practices, and the practicability, including the time and cost involved, of doing so.
Observations
3.95 Trulioo staff advised the OAIC that certain types of personal information collected during identity verification transactions are retained in the GlobalGateway database, and can be accessed via the GlobalGateway Portal. The retained personal information includes names, dates of birth, government identifiers, addresses, and whether the individual was successfully matched or not. Personal information is not necessarily retained in all identity verification transactions. Where personal information is retained, as noted at 3.21, Trulioo is entitled to do so.
3.96 Trulioo has legislative obligations to retain certain records. For example, under s 286 of the Corporations Act 2001 (Cth), Trulioo is obligated to keep financial records for a period of seven years. Under s 107 of the Anti-Money Laundering and Counter-Terrorism Financing Act 2006 (Cth), Trulioo is also required to retain transaction records for seven years. These records include personal information relating to individuals.
3.97 The OAIC understands that Trulioo retains these records for a number of reasons in additional to these legislative requirements. For example, Trulioo’s business users may rely on records of identity verification transactions for auditing purposes, such as to establish or verify that a transaction has occurred, and when it occurred. Trulioo also refers to retained data for customer service purposes, such as if one of their business users needs to locate a specific transaction record.
3.98 The OAIC understands that Trulioo’s retention of records has not yet reached the legislated minimum length of time.
3.99 Trulioo has documented its current policy on the retention and disposal of information systems and information assets. The ISP states that the retention of records must be ‘in accordance with legislative, business, and contractual requirements’. The Acceptable Use Policy further details this high-level statement, and assigns the responsibility for ensuring that these requirements are met to the owner of the information systems and assets.
3.100 The Acceptable Use Policy also states that confidential information assets, such as transaction records containing personal information, must be disposed of securely when there are ‘no longer needed’. The document details how that disposal should be carried out at that time.
Analysis
3.101 Trulioo’s legislative obligations dictate the minimum length of time it needs to retain financial and transaction records that contain individuals’ personal information. As Trulioo has not yet reached that minimum length of time, this retention is supported by applicable legislation. Outside of these obligations, Trulioo’s retention of personal information is subject to business users’ needs. Trulioo’s documentation of its policy on the retention and disposal of data is good practice.
3.102 When Trulioo reaches that minimum length of time, Trulioo may wish to update or further detail its policy of disposing of information that is ‘no longer needed’. The OAIC suggests that Trulioo continues to review its policy on the retention and disposal of data containing personal information, to ensure that it will reflect its approach to the retention or disposal of data.
3.103 As noted at 3.96, Trulioo retains a range of personal information in the GlobalGateway database. [redacted]. The OAIC understands that Trulioo’s retention of personal information to this extent is a reflection of arrangements that it has made with its business users.
3.104 As with any database containing personal information, the risk profile of the GlobalGateway database will increase over time commensurately with the volume of personal information that it holds.
3.105 With this in mind, the OAIC also suggests that Trulioo periodically reviews the necessity of retaining the full range of the personal information that it collects as set out in 3.103, or whether business user requirements could be met with a subset of this range, as one way to manage any future risks associated with that information.
Part 4: Recommendations and responses
Recommendation 1 – review of information security documentation
OAIC recommendation
4.1 Trulioo:
- ensures the consistent and timely review of its information security documentation
- creates and implements detailed policies, as needed, to further support its high-level documentation, and disseminates these policies to staff.
Response by Trulioo to the recommendation
4.2 Trulioo responses:
- The documentation, policies, and related procedures associated with Recommendation 1 have since been reviewed and addressed.
- Trulioo provides services globally, and as such, ensures customizable record keeping requirements for all jurisdictions according to legislative and regulatory obligations. The retention of personal information is optional. With clarifications from the OAIC, Trulioo will soon have completed further system enhancements to eliminate potential risks identified in this report.
- Trulioo is a Processor as defined by European regulatory standards. As such, Trulioo actively and transparently adheres to any end-user information requests or direction from the related Controller/Business User.
Part 5: Description of assessment
Objective and scope
5.1 The objective of this assessment was to establish whether Trulioo is handling personal information throughout the document verification process in accordance with the APPs.
5.2 The assessment examined whether Trulioo is collecting personal information, and notifying individuals of that collection, in accordance with APPs 3 and 5. The assessment also considered whether Trulioo’s personal information storage and security arrangements are reasonable in the circumstances to protect personal information from misuse, interference, loss, unauthorised access, modification or disclosure, in accordance with APP 11.
5.3 Apart from the DVS, there are other means through which an issuing agency can confirm the validity of documents. Some issuing agencies use GSPs to confirm the validity of documents both through the DVS and otherwise. The scope of this assessment was limited to Trulioo’s handling of personal information only through the DVS.
Privacy risks
5.4 The OAIC makes recommendations to address ‘high’ and ‘medium’ privacy risks. For more information about these privacy risk ratings, see the OAIC’s ‘Privacy risk guidance’ at Appendix A. Further detail on this approach can be found in Chapter 7 of the OAIC’s Guide to privacy regulatory action.
5.5 The OAIC has made one recommendation to address a medium privacy risk identified during this assessment. A recommendation is a suggested course of action or a control measure that, if put in place by Trulioo, will (in the opinion of the OAIC) minimise the privacy risks identified around how it handles personal information.
Timing, location and assessment techniques
5.6 Trulioo is based in Vancouver, Canada. Trulioo provided the OAIC with copies of relevant policy and procedure documents in response to the OAIC’s information request. The OAIC then conducted the fieldwork component of the assessment via videoconference on 21, 22, 28, and 30 June 2017. The OAIC interviewed staff in various roles at Trulioo during the fieldwork.
Reporting
5.7 The OAIC publishes final assessment reports in full, or in an abridged version, on its website. All or part of an assessment report may be withheld from publication due to statutory secrecy provisions, privacy, confidentiality, security or privilege. This report has been published in an abridged version.
Appendix A: Privacy risk guidance
Privacy risk rating | Entity action required | Likely outcome if risk is not addressed |
|---|---|---|
High risk | Immediate management attention is required. |
|
Medium risk | Timely management attention is expected. |
|
Low risk | Management attention is suggested. |
|
Footnotes
[1] Can be downloaded at www.dvs.gov.au/users/Documents/DVSPolicyandGuidelines.pdf.
[2] Can be downloaded at www.dvs.gov.au/users/Documents/BUtermsandconditions.pdf.
[3] A government related identifier is a number, letter or symbol, or a combination of any or all of those things, that has been assigned by an agency, a State or Territory authority, an agent of an agency or authority, or a contracted service provider for a Commonwealth or State contract.
[4] Trulioo, About Us, 2017, Trulioo website www.trulioo.com/company/about-us/.
[5] An API refers to an application programming interface, which here refers to a defined interface through which identity verification interactions will occur.
[6] Trulioo, Identity Verification, 2017, Trulioo website https://www.trulioo.com/developers/identity-verification/.
[7] Available for download at https://www.dvs.gov.au/users/Documents/DVSGatewayServiceProviderAgreement.pdf.
[8] Refer to APP 5.2(b).
[9] An ISMS is a framework of documented policies, procedures, and manuals that include the information security controls involved in an organisation’s risk management process.
[10] ISO 27001 is a standard for an ISMS, published by the International Organisation for Standardisation.
[11] A RACI (an acronym for Responsible, Accountable, Consulted, and Informed) chart outlines the roles and responsibilities for a company’s activities and processes.
[12] Multi-factor authentication is a method of securing access to a system or its contents by requiring more than one type of authentication to verify a user’s identity. A common example is logging into a website with a password, and being requested to enter an additional one-time password that the website sends to the user’s phone number or email address.

