-
On this page
Part 1: Executive summary
1.1 This report outlines the findings of the Office of the Australian Information Commissioner’s (OAIC) privacy assessment of data matching activities undertaken by the Department of Health and Aged Care (Health). We assessed Health’s program matching the Medicare Benefits Schedule (MBS) and Pharmaceutical Benefits Scheme (PBS) data.
1.2 We assessed whether Health was matching (and handling) this data in accordance with Part VIIIA of the National Health Act 1953 (Cth) (NH Act). We also assessed whether Health was matching the data in accordance with the National Health (Data‑matching) Principles 2020 (DM Principles), which were made under Part VIIIA of the NH Act.
1.3 This was our second assessment of Health’s data matching under these provisions.[1]
1.4 We identified 2 high risks and one medium risk relating to Health’s policies and procedures:
- one of Health’s public-facing documents did not accurately explain the source of the data. This was a medium risk as Health staff may not understand they need to inform Services Australia in the event information needed to be corrected, plus it could mislead the public
- we recommended that Health should ensure documents, especially public-facing documents, correctly reference Services Australia as the source of the data for MBS and PBS data matching.
- the ‘Risks and Sensitivities’ section of Health’s Technical Standards document stated there were no risks related to the data matching, despite risks implied throughout the document and the risks inherent in data matching (see paragraph 2.1). This was a high risk as in order to control and mitigate risks they must first be identified
- we recommended that Health must undertake a detailed risk analysis to identify any possible risks to personal information within the program matching MBS and PBS data and include this in the Technical Standards.
- Health did not have sufficient information in its processes and procedures relating to the destruction of data. This was a high risk as Health could inadvertently retain the data and incorrectly use or disclose data that it no longer had authority to hold
- we recommended that Health must review its destruction processes and procedures to ensure Health can meet the destruction obligations in the DM Principles, clearly outlining when, how and by whom the data should be destroyed.
1.5 We identified 2 high risks relating to Health’s record-keeping and made recommendations to address these risks
- Health kept inadequate records of when it received the source data, leading to potential version control issues and the risk that the data it was relying on was outdated
- we recommended that Health must maintain records reflecting the date it collected the source data for the purposes of data matching.
- In accordance with the DM Principles, Health is required to keep records of the data that has been destroyed. We found that Health was not keeping sufficiently detailed records about the destruction of datasets. This created a risk that Health might not destroy the data, and incorrectly use or disclose data that it no longer had authority to hold
- we recommended that Health must ensure records include an adequate description of the personal information destroyed, or results of matching destroyed under subsections 15(1), 16(1) and 17(1) of the DM Principles.
Part 2: Data Matching
Data Matching Principles
2.1 Data matching involves bringing together data from different sources and comparing it. Government agencies often match data to identify people for investigation (for example, for being paid benefits for which they may not be entitled). But data matching can create risks to personal privacy because it can involve analysing information about large numbers of people without prior cause for suspicion, and may generate new personal information.[2] This is particularly the case with sensitive personal information, such as health information.
2.2 The NH Act allows the Chief Executive Medicare (CEM) to match data, including MBS and PBS data, for the purposes permitted under s 132A of the NH Act.
2.3 The definitions of permitted purpose, under s 132A, include a) identifying whether a person may have, under a Medicare program, claimed or been paid a benefit that exceeds the amount of the benefit that was payable to the person and b) recovering overpayments of benefits under a Medicare program.[3]
2.4 Recognising the risks of data matching, Part VIIIA of the NH Act outlines obligations for agencies matching certain datasets, including MBS and PBS data. Further, s 132F of the NH Act specifically requires the Health Minister to, by legislative instrument, make principles in relation to the matching of information permitted under Part VIIIA. These are the DM Principles.
The Data Matching Process
2.5 The Chief Executive Officer of Services Australia is appointed as the CEM by the Secretary of the Department of Health under Section 4A of the Human Services (Medicare) Act 1973.
2.6 Part VIIIA of the NH Act enables the CEM to match certain information for permitted purposes, which are Medicare compliance and related administrative purposes. This includes detecting instances of fraud, inappropriate practice and incorrect claiming in relation to Medicare programs including MBS and the PBS.
2.7 Under subsection 6(9) of the NH Act the CEM has the delegated power to match data to Health . Under this arrangement, Services Australia may disclose MBS and PBS claims information to Health for the purposes of MBS and PBS data matching.
2.8 Health holds its copies of the MBS and PBS databases in an Enterprise Data Warehouse and conducts routine data matching of health practitioners’ MBS claims data, and PBS claims data, in order to identify possibly fraudulent claims.
2.9 Health informed us that it matches those datasets in secure environments subject to strict access and security controls. Health also informed us that only authorised Health staff can access the datasets when required as part of an approved data matching program. We did not assess those controls.
2.10 Where the results of data matching warrant further investigation, Health’s compliance officers will audit or investigate the claims.
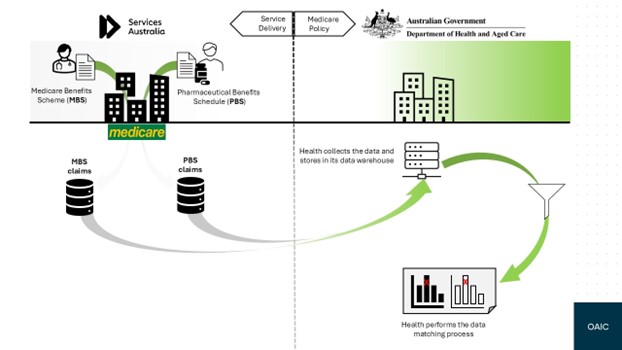
2.11 Health maintains a Standard Operating Procedure which provides:
- high level steps for destroying data and updating related records
- Technical Standards documentation
- repositories for records of destruction
Part 3: Findings
Our Assessment
3.1 Health has conducted MBS and PBS data matching under Part VIII of the NH Act and the DM Principles. We therefore assessed Health’s compliance against the obligations of the NH Act and DM Principles.
3.2 Part VIIIA of the NH Act does not set out specific obligations for handling data, but sets out what the Health Minister must include in the DM Principles. As such, our analysis below only outlines Health’s compliance against the provisions in the DM Principles.
3.3 Table 1 summarises Health’s obligations under the DM Principles and includes our findings of their compliance against those obligations. Where we found partial or non-compliance, we include our assessment of risk.
DM Principles section and obligation | Finding |
|---|---|
Ss 1-4 of the DM Principles provide the Name, Commencement, Authority and Definitions. These do not form part of our assessment. | N/A |
S 5: The CEM must publish materials prescribed in that section on the internet. | Partially compliant, medium risk (see para 3.5) |
S 6: The CEM must prepare and maintain written Technical Standards to govern the conduct of each data matching program which include the information set out in subs 6(2)(a-e). | Partially compliant, high risk (see para 3.11) |
S 7: Conduct an evaluation of privacy practices relating to authorised matching within 3 years of the commencement of that matching. | Compliant |
S 8: The CEM must establish and maintain a publicly available register of the kinds of information matched by the CEM. | Compliant |
S 9: The CEM must include specific information in the publicly available register for each kind of information matched. | Compliant |
S 11: The CEM must keep records of the information matched under subsection 132B(1) of the NH Act. | Compliant |
S12: The CEM must keep specific records for each authorised data-matching program. | Partially compliant, high risk (see para 3.20) |
S13: The CEM must keep records of personal information destroyed under subsections 15(1), 16(1) and 17(1) of the DM Principles. | Partially compliant, |
S14: The records mentioned in Ss 11-13 must be sufficient to enable the Australian Information Commissioner to conduct an assessment. | Compliant |
Ss 15-17: The CEM must, within 90 days of a decision that personal information, matched information, or personal information that won’t be matched is no longer needed, destroy that information. | Partially compliant, high risk (See para 3.35) |
S18: The CEM must take reasonable steps to ensure that personal information is accurate, complete, and up to date. | Compliant |
S19: The CEM must not match information for a permitted purpose unless they are satisfied that the matching is reasonably necessary. | Compliant |
S20: The CEM must decide on necessary data fields and subjects and in making the decision, consider how to minimise data fields and personal information. | Compliant |
3.4 The following headings reflect the headings applied in the DM Principles.
Preliminary (Part 1, sections 1-4)
3.5 These sections provide the DM Principles’ name, commencement, authority and definitions. Part 1 does not form part of the assessment.
Good privacy practice (Part 2, sections 5-7)
3.6 Part 2 of the DM Principles concerns good privacy practice and outlines the requirements regarding publishing, the technical standards, and the evaluation of privacy practices.
Section 5 – Publishing information about authorised information-matching
3.7 Section 5 of the DM Principles requires the CEM to publish, on the internet, materials prescribed in that section.
3.8 Health has provided a link to information published, on its public facing website, under the title ‘Our Medicare compliance activities’[4], along with a document titled Public register - data matching activities.[5]
3.9 We found that there were inconsistencies between Health’s public facing documents and internal documentation when referring to the source of the data used for matching. Health’s Public Register – Data Matching Activities document cites the Department of Health and Aged Care as the data source, whilst several internal documents referenced Services Australia as the source. As Services Australia provides the MBS and PBS claims data to Health, Services Australia is the source.
3.10 We considered this to be a medium risk . By referring to Health as the data source, the document is not accurate or transparent about the information flow. This creates the risk that Health staff may not inform Services Australia in the event the information needs to be corrected, in addition there is the risk the public may be misled about the origin of the data.
3.11 Health has partially complied with s 5 of the DM Principles.
Recommendation 1
Health should ensure documents, especially public-facing documents, correctly reference Services Australia as the source of the data for MBS and PBS data matching.
Section 6 – Technical standards for authorised data-matching programs
3.12 Section 6 of the DM Principles requires the CEM to prepare and maintain written Technical Standards to govern the conduct of each data matching program. The Technical Standards must include the information set out in subs 6(2)(a-e) of the DM Principles.
3.13 Subsection 6(2)(c) requires that the Technical Standards should include any risks identified in relation to the program and how those risks will be addressed.
3.14 Health provided technical standards documents for our assessment, including the Technical Standards Report. The ‘Risks and Sensitivities’ section of this document states there are ‘no risks and sensitives particularly associated with the matching of these two datasets under these conditions.’ The Technical Standards Report we reviewed did not provide any analysis to justify this statement.
3.15 However, we noted in the Technical Standards document various statements that imply risk, for example, in other areas of the document there is reference to data age, quantitative changes, and cleansing processes (with reference to quality) and environment (with reference to the reproduction of results).
3.16 Further, as we note in paragraph 2.1 of this report, data matching is inherently a high-risk activity, particularly in relation to sensitive personal information such as MBS and PBS claims data.
3.17 We therefore consider that, in the absence of detailed risk analysis, it is unlikely that there are ‘no risks and sensitives particularly associated with the matching of MBS and PBS data.
3.18 We considered this to be a high risk . By not adequately identifying and conveying the risks associated with data matching activities in the technical standards, there is an increased likelihood of the risk eventuating. Where necessary controls associated with risks are not applied and monitored, there are potentially greater consequences of associated harm or damage arising.
3.19 Health has partially complied with s 6 of the DM Principles.
Recommendation 2
Health must undertake a detailed risk analysis to identify any possible risks to personal information within the program matching MBS and PBS data and include this in the Technical Standards.
Publicly available register (Part 3, Sections 8 – 9)
3.20 Health has complied with Sections 8 – 9 of the DM Principles.
Record-keeping (Part 4, Sections 11 – 14)
Section 12 – Records for authorised data matching programs
3.21 Section 12 sets out specific records that should be maintained in relation to authorised data‑matching programs.
3.22 Paragraph 12(1)(e) of the DM Principles requires, if the information that was matched for the program was obtained by the CEM from another person or entity for the purpose of facilitating the matching, that records are kept showing the date the information was obtained.
3.23 We were unable to establish from the records provided to us that Health kept records of the date it obtained either the MBS or PBS datasets from Services Australia.
3.24 We considered this to be a high risk . Without this information, Health cannot be sure of the validity of the data (for example whether it was subsequently corrected). This creates the risk of incorrect matches leading to unwarranted enforcement action.
3.25 Health has partially complied with s 12 of the DM Principles.
Recommendation 3
Health must maintain records reflecting the date it obtained from the source the data it used for the purpose of facilitating the matching.
Section 13 – Records of destruction of information and results
3.26 Subsection 13(1) of the DM Principles requires Health, as the delegate of the CEM, to keep records of personal information destroyed under subsections 15(1), 16(1) and 17(1) of the DM Principles.
3.27 During the assessment Health informed us that its Risk Analytics Section (RAS) maintains a data-matching register. Health noted that where a criterion for destruction was triggered, as per the Standard Operating Procedure, destruction actions would be recorded in the register indicating the data destroyed and timing of destruction actions. Additionally, where destruction occurred, data analytics staff would update the technical standards document on milestones of destruction.
3.28 However, we were unable to identify from the register adequate evidence of the description of destruction of information. Further, we were unable to identify from the register dates or a specific period relating to instances of destruction.
3.29 We considered this to be a high risk . By not recording sufficient information to identify data sets, and confirm that those datasets have been destroyed (i.e., when no longer needed), these datasets may be incorrectly retained. This creates a risk that Health could incorrectly use or disclose datasets that it no longer had authority to hold.
3.30 Health has partially complied with s 13 of the DM Principles.
Recommendation 4
Health must ensure records include an adequate description of the personal information destroyed, or results of matching destroyed under subsections 15(1), 16(1) and 17(1) of the DM Principles.
Destruction of personal information and results of matching (Part 5, Sections 15 – 17)
3.31 Section 15 the DM Principles require Health, as the delegate of the CEM, to take reasonable steps to destroy personal information that has been matched when no longer needed, within 90 days after the information ceases to be needed (s 15).
3.32 Section 16 the DM Principles require Health, as the delegate of the CEM, to take reasonable steps to destroy the results of the matching of information when no longer needed, within 90 days after the results cease to be needed (s 16).
3.33 Section 17 the DM Principles require Health, as the delegate of the CEM, to take reasonable steps to destroy personal information held that was obtained by the CEM, and the information is not intended to be matched, within 90 days after becoming aware the information is not intended to be matched (s 17).
3.34 Health informed us that there is a 2-year threshold of keeping information for compliance activities. Health noted, its compliance processes can often take longer than the 2-year threshold listed its Data Destruction SOP. Health provided a Data Destruction Standard Operating Procedure (SOP) document along with the Data Matching Registry document to evidence compliance with ss 15-17.
3.35 Health has listed events in the SOP that would trigger destruction obligations under ss 15-17, however, these events were not clearly defined, and do not clearly correlate with the obligations under ss 15-17. Further, it was not evident from this document how triggers are identified by the relevant staff with responsibility for the destruction of data.
3.36 The SOP does not outline, nor demonstrate, what are reasonable steps for destroying the data. Including reasonable steps is necessary in order to comply with ss 15-17.
3.37 We considered this to be high risk . By not having sufficiently detailed processes, and records to evidence destruction of discrete datasets, these datasets may be incorrectly retained. This creates a risk that Health could incorrectly use or disclose datasets that it no longer had authority to hold.
3.38 Health has partially complied with ss 15-17 of the DM Principles.
Recommendation 5
Health must review its destruction processes and procedures to ensure Health can meet the destruction obligations in the DM Principles, clearly outlining when, how and by whom the data should be destroyed. As part of this, Health should:
- consider more clearly defining key position-holders, and responsibilities, notifications and triggers for specific activities required under this section
- review the period of time that information is able to be retained under sections 15 and 16 of the DM Principles, including identifying the basis for that retention (para 15(3)(a)).
3.39 We acknowledge, at the time of compiling this assessment report, Health had identified areas for improvement and commenced a review of its data destruction processes and records documentation.
Accuracy, completeness, and currency of personal information (Part 6, section 18)
Section 18 – Accuracy, completeness, and currency of personal information.
3.40 Part 6, s 18 of the DM Principles requires Health, as the CEM Medicare, to take reasonable steps to ensure that personal information that is matched is accurate, complete and current. These steps should include quality assurance checks.
3.41 Health has complied with section 18 of the DM Principles.
Decisions about matching of information (Part 7, sections 19-20)
3.42 Part 7 of the DM Principles relates to decisions about matching of information along with decisions about necessary data fields and subjects.
3.43 Health has complied with Part 7 of the DM Principles.
Part 4: Recommendations and Responses
4.1 Prior to publication, the OAIC provided Health a copy of this report with our findings and recommendations. We gave Health the opportunity to respond the recommendations. This Part outlines each recommendation and Health’s response to each recommendation.
Recommendation 1
Health should ensure documents, especially public-facing documents, correctly reference Services Australia as the source of the data for MBS and PBS data matching.
4.2 Health response to Recommendation 1
Accepted
Health will update the Public Register for data matching activities to ensure that, when appropriate, Services Australia is recognised as the source of MBS and PBS data. These changes will also be reflected in the Technical Standards to ensure the source of the MBS/PBS data is Services Australia.
Recommendation 2
Health must undertake a detailed risk analysis to identify any possible risks to personal information within the program matching MBS and PBS data and include this in the Technical Standards.
4.3 Health response to Recommendation 2
Accepted
We acknowledge the necessity of conducting further assessments on future data matching programs. While the current Technical Standards briefly addresses risk associated with the data matching, a more thorough examination of any potential threats to information or data collection will be undertaken and documented for the program. If no threats are identified after the analysis, the reasons for the absence of risk will be clearly defined. To avoid misunderstandings for external stakeholders, we will suggest being more prescriptive when using the word "risk". The risk analysis should focus on identified risk/risk mitigation of privacy concerns related to the handling of personal information, rather than compliance issues. Health will ensure that analysts provide evidence that an assessment has been completed.
Recommendation 3
Health must maintain records reflecting the date it obtained from the source the data it used for the purpose of facilitating the matching
4.4 Health response to Recommendation 3
Accepted
Health Data Governance will collaborate with the Risk Analytics team to ensure Technical Standards incorporate the earliest data received/included in matching from date
Recommendation 4
Health must ensure records include an adequate description of the personal information destroyed, or results of matching destroyed under subsections 15(1), 16(1) and 17(1) of the DM Principles.
4.5 Health response to Recommendation 4
Accepted
Health has implemented a new policy on data destruction. The policy includes the necessary records to verify that data destruction has been completed. Health may review the policy to explicitly include the inability to retrieve any destroyed data.
Recommendation 5
Health must review its destruction processes and procedures to ensure clarity about when, how and by whom the data should be destroyed. As part of this, Health should
- consider more clearly defining key position-holders, and responsibilities, notifications and triggers for specific activities required under this section
- review the period of time that information is able to be retained under section 15 and 16 of the DM Principles, including identifying the basis for that retention (para 15(3)(a)).
4.6 Health response to Recommendation 5
Accepted
Health has developed a data destruction policy which has been endorsed by internal stakeholders. The policy is clear and concise in relation to data destruction and associated triggers for destruction. This policy provides explicit guidance and assigns responsibility to Health, rather than the initial data team, for ensuring that any data matching program meeting a destruction trigger point is properly destroyed. The policy has a focus on roles and responsibilities and the notification provisions required to ensure triggers for destruction are actioned and recorded.
Part 5: Description of assessment
Role of the Australian Information Commissioner
5.1 This assessment was conducted in accordance with Section 33C(1)(f) of the Privacy Act 1988 (Cth) which provides for the Australian Information Commissioner to conduct an assessment to determine whether the matching of information under Part VIIIA of the National Health Act 1953 (Cth) (National Health Act), is in accordance with that Part.
Objective, Scope, and Methodology of the assessment
Objective
5.2 The objective of this assessment was to determine whether Health was matching and handling MBS and PBS information in accordance with Part VIIIA of the NH Act and DM Principles made by the Minister under subsection 132F (1) of the NH Act.
Scope
5.3 Specifically, the assessment considered:
- Health’s data-matching and information-handling of MBS and PBS datasets
- Health’s compliance with its obligations under Part VIIIA of the NH Act and the DM Principles.
5.4 The scope of this assessment did not include:
- subsections 132B (2)-(3) of the National Health Act
- compliance of the source entity for the MBS and PBS data (Services Australia).
5.5 While the assessment scope did not specifically consider compliance with the Australian Privacy Principles (APPs) and the OAIC’s Guidelines on Data-Matching in Australian Government Administration, we had regard to these when interpreting the application of Part VIIIA of the NH Act and the DM Principles.
Methodology
5.6 This was a compliance-based assessment.
5.7 The assessment involved a desktop review of papers followed online interviews with Health.
5.8 Where the OAIC found partial compliance, we assessed the risk of that non-compliance and made recommendations about how to address the compliance and risks. These recommendations are set out in Part 4 of this report.
5.9 Where the OAIC identified privacy risks, we assessed those risks according to the OAIC’s Privacy risk guidance ( see Appendix A ).
5.10 OAIC assessments are conducted as a ‘point in time’ exercise; that is, our observations, findings and recommendations are applicable to the time period in which the assessment was undertaken. In this assessment, we examined Health’s policies, procedures and systems as at early October 2024.
5.11 To assess Health’s compliance, we applied the DM Principles with additional consideration for the OAIC’s Guidelines on data matching in Australian Government administration[6] (DM Guidelines). These Guidelines, issued under section 28(1)(a) of the Privacy Act, are voluntary but represent the OAIC’s view on best practice with respect to undertaking data matching activities.
5.12 While the data matching by Health is not conducted under the OAIC’s DM guidelines, several of the obligations in the DM Principles are similar to the DM Guidelines. Accordingly, when assessing Health’s obligations under the DM Principles, the OAIC has had regard to the Data Matching Guidelines. We also had regard to the Australian Privacy Principles (APP), and the National Health (Privacy) Rules 2021[7].
Part 6: Appendices
Appendix A – Privacy risk guidance
Privacy risk rating | Entity action required | Likely outcome if risk is not addressed |
|---|---|---|
High risk Entity must, as a high priority, take steps to address mandatory requirements of Privacy and related legislation | Immediate management attention is required This is an internal control or risk management issue that if not mitigated is likely to lead to the following effects |
|
Medium risk Entity should, as a medium priority, take steps to address Office expectations around requirements of Privacy and related legislation | Timely management attention is expected This is an internal control or risk management issue that may lead to the following effects |
|
Low risk Entity could, as a lower priority than for high and medium risks, take steps to better address compliance with requirements of Privacy and related legislation | Management attention is suggested |
|
[1] The first assessment of data-matching under Part VIIIA of the National Health Act 1953 (Cth) targeted the ‘Practice Incentives Program eHealth Incentive’ (ePIP). (See Data-matching conducted by the Department of Health and Aged Care: Practice Incentives Program eHealth Incentives Compliance Program).
[2] For more information, see Government data matching
[3] See s 132A of the NH Act, which defines permitted purposes of data matching.

